Part Of Our
Protect from malicious hackers by
Understanding your entry points
As the number of applications and services your company provides grows and your use of the Internet increases, it can be difficult to understand your company’s entry points and more importantly any weaknesses in them.
Anybody who wants to protect customer and company data, or who needs to ensure their systems are protected from malicious hackers will need to assess how well their current security infrastructure is coping with the increasing number of threats and exposures.
A penetration test is designed to specifically target your company’s infrastructure and identify your key assets and the protection they are provided. It begins by profiling your systems and looking for weaknesses or oversights that can be exploited and then using this information to penetrate further into your network. Once the initial identification stage has been completed we can test your most critical systems as either trusted or untrusted users. We use all known vulnerabilities to baseline your security posture.
Typical Targets
Typical targets include but are not limited to:
- E-mail servers
- Research & Development systems
- Database servers and storage
- Websites and E-commerce systems
- Remote entry points
- Trusted systems (including your security systems)
We will sign a Non-Disclosure Agreement with an executive sponsor in your company so all information identified or discussed remains confidential. Once the test has been performed we will provide a report on the findings and brief you on-site on how these weaknesses can be eradicated. Our consultants are CISSP certified and as such are well versed in not just your technical security infrastructure but how this interfaces into your policies, procedures and data security requirements.
Why choose us?
We’re ready to talk when you are. Leverage our heritage and discover why our longevity, knowledge and ability to solution manage for our clients is second to none.
Our customers
We work closely with our customers across multiple business cycles to ensure they get the best business outcome from their investments in digital platforms, data and IoT as their digital strategy evolves. We see ourselves as a business partner in the fullest sense of the term.
Our experience
With a solid market perspective, over 20 years’ experience in delivering IBM state-of-the-art enterprise solutions, we can support businesses to turn their ambitions into reality. Whether you’re looking to enhance your current IT infrastructure or adopt new digital capabilities, Maple has the experience and know-how to help.
From the Mouth of the client
‘Ok’, is not ok
Maple’s depth of knowledge and skills around OS/400 and our system allowed our migration to the latest Power system happen far quicker than we thought.IT Global iSeries Lead | International Bank
They deliver commercial knowledge that is unprecedented and, because of that, they have become a key part of our team.Leading Insurance PLC | CIO

The Maple Blueprint
Please select a leaf segment to discover more about the services Maple offers.
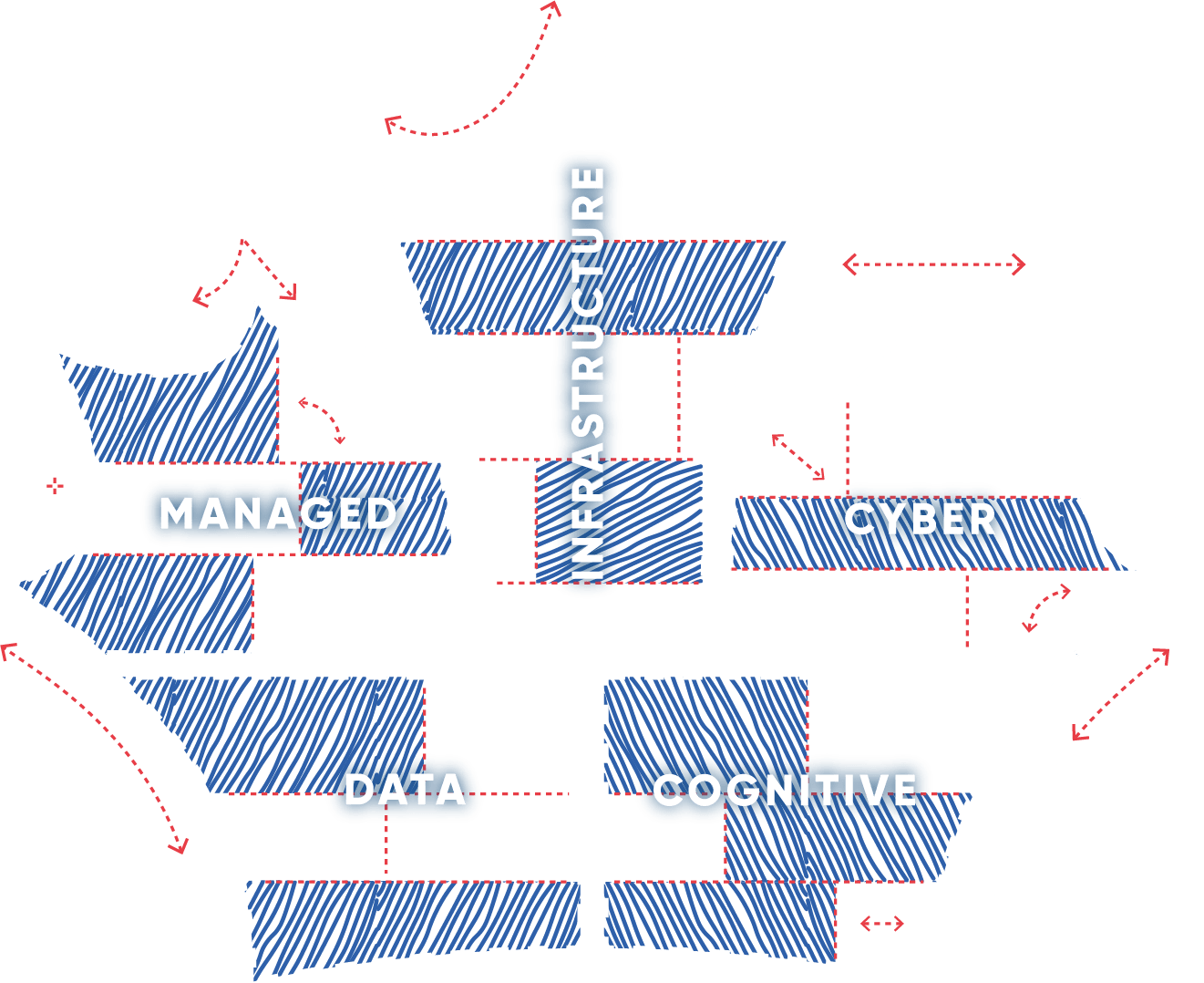
1. Infrastructure
Services
- IBM Power - IBM i, Storage, IBM AIX Physical & IAAS/cloud
- After warranty Maintenance & Software Licensing optimisation
- On demand and on premise compute with multi cloud
- HP or Lenovo compute and storage
- NetApp Storage
2. Cyber
Services
- Network security and AI driven threat protection
- Managed Security and Soc
- Fraud Detection and prevention
3. Cognitive
Services
- Enterprise A.I
- A.I optimised Platforms
- Service Now
- A.I and Machine Learning at Scale
- Business analytics
4. Data
Services
- Cloud replication & backup to the cloud
- Disaster Recovery
- High Availability
- Cloud Orchestration
- Automated data protection
5. Managed
Services
- iSeries remote management
- Rapid Access
- IAAS/PAAS
- Storage management
- Systems management